Insider threats have become a growing concern for organizations of all sizes and industries. These threats can cause significant damage to a company’s reputation, finances, and overall security. In this comprehensive guide, we will delve into the various aspects of insider threats, including their definition, types, motivations, and prevention strategies.
What is an Insider Threat?
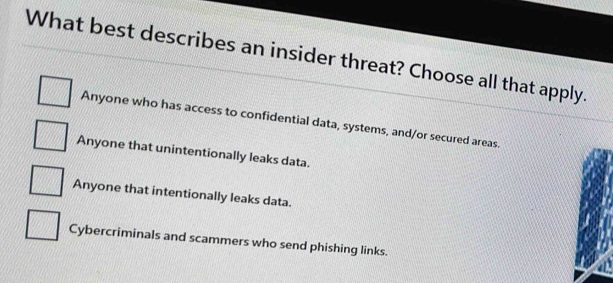
An insider threat refers to any malicious or unauthorized action carried out by an individual with authorized access to an organization’s systems, data, or other assets. This could include employees, contractors, vendors, or partners who have been granted access to sensitive information or infrastructure.
Unlike external threats, which originate from outside an organization, insider threats pose a unique challenge due to the trusted access and knowledge that insiders possess. They can exploit their position of trust to cause harm to the organization, making them difficult to detect and prevent.
Which Best Describes an Insider Threat?
To better understand insider threats, let’s take a closer look at some common categories that best describe them:
Employees
Current or former employees are often the first category that comes to mind when discussing insider threats. These individuals have authorized access to company systems and data, making it easier for them to carry out malicious activities without raising suspicion.
Employees may have a variety of motivations for committing insider threats, such as personal grievances, financial gain, or even unintentional actions due to negligence or lack of awareness.
Contractors
Third-party personnel, such as contractors, also pose a potential insider threat. Theseindividuals may have temporary access to company systems and data, making it difficult for organizations to monitor their activities closely.
Contractors may not have the same level of loyalty or accountability as permanent employees, making them more susceptible to engaging in malicious actions.
Insider Threat Indicators
There are several indicators that can help organizations identify potential insider threats. These include:
- Changes in behavior: An employee who suddenly starts exhibiting unusual or erratic behavior, such as increased aggression or isolation, could be a sign of an insider threat.
- Financial troubles: Employees facing financial difficulties may be more likely to engage in fraudulent activities to alleviate their financial stress.
- Unauthorized access: Insiders may attempt to access sensitive information or systems outside of their job responsibilities.
- Disgruntled employees: Individuals who feel wronged by the organization or have a negative attitude towards their job may be more likely to engage in malicious actions.
It is essential for organizations to regularly monitor these indicators and take appropriate action to prevent insider threats from occurring.
Types of Insider Threats
Insider threats can take various forms, depending on the individual’s motivation and the type of harm they intend to cause. Some common types of insider threats include:
- Data theft: Insiders may steal sensitive information, such as customer data, trade secrets, or financial records, for personal gain or to sell to competitors.
- Sabotage: An insider may intentionally disrupt or damage critical systems or infrastructure, causing significant financial and reputational damage to the organization.
- Fraud: Insiders may engage in fraudulent activities, such as altering financial records or creating fake accounts, to embezzle funds from the organization.
- Espionage: Insiders may work with external actors to gather sensitive information about the organization, its operations, or its clients for malicious purposes.
Preventing Insider Threats
Preventing insider threats requires a multi-faceted approach that involves both technological solutions and human intervention. Here are some strategies organizations can implement to mitigate the risk of insider threats:
- Employee training and awareness: Regularly educating employees on the importance of cybersecurity, data protection, and recognizing potential insider threat indicators can help prevent malicious actions.
- Access control: Limiting access to sensitive information and systems only to those who need it can reduce the risk of insider threats.
- Monitoring and auditing: Organizations should regularly monitor and audit employee activities to identify any suspicious behavior or unauthorized access.
- Background checks: Conducting thorough background checks on new employees and contractors can help identify any red flags that may indicate a potential insider threat.
Conclusion
Insider threats pose a significant risk to organizations, and their impact can be devastating. By understanding what an insider threat is, its various forms, and how to prevent them, organizations can take proactive measures to protect themselves from these malicious actors. It is crucial for organizations to have a comprehensive insider threat program in place to detect, prevent, and respond to these threats effectively.

Related Posts: